一、漏洞详情
Windows Server是由微软开发的操作系统系列,专为服务器环境设计,用于管理网络、数据存储和应用程序的运行。它为企业和组织提供了稳定、可靠的服务器平台,支持各种规模的网络基础设施。
近日,监测到官方修复Windows远程桌面授权服务远程代码执行漏洞(CVE-2024-38077),该漏洞存在于Windows远程桌面许可管理服务(RDL)中,攻击者无需任何权限即可实现远程代码执行,获取服务器最高权限。由于在解码用户输入的许可密钥包时,未正确检验解码后数据长度与缓冲区大小之间的关系,导致缓冲区溢出。
建议受影响用户做好资产自查以及预防工作,以免遭受黑客攻击。
二、影响范围
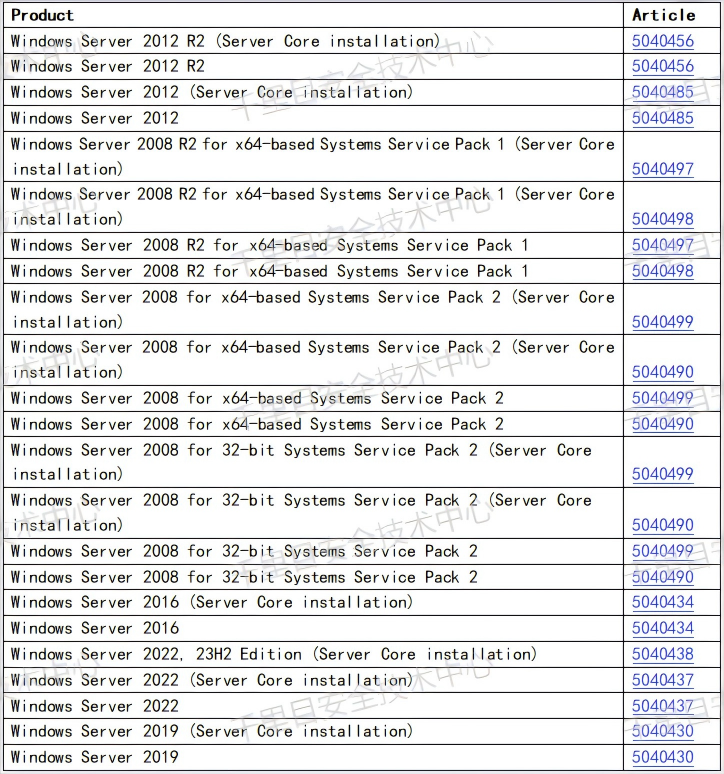
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows Server 2022, 23H2 Edition (Server Core installation)
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows Server 2019 (Server Core installation)
Windows Server 2019
三、修复建议
微软官方已发布补丁公告,建议尽快查看官网公告更新安全补丁。
修复方法
上面是官方的描述,下面说人话,写了一个脚本可以来检查是否受这个漏洞影响
# 获取当前系统的版本信息
$currentVersion = (Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion").CurrentVersion
$currentBuild = (Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion").CurrentBuildNumber
$currentUBR = (Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion").UBR
# 组合当前系统的版本号
$currentFullVersion = "$currentVersion.$currentBuild.$currentUBR"
# 定义安全版本号的列表
$safeVersions = @(
@{Version="6.3"; Build="9600.22074"; Description="Windows Server 2012 R2"},
@{Version="6.2"; Build="9200.24975"; Description="Windows Server 2012"},
@{Version="6.1"; Build="7601.27219"; Description="Windows Server 2008 R2"},
@{Version="6.0"; Build="6003.22769"; Description="Windows Server 2008"},
@{Version="10.0"; Build="14393.7159"; Description="Windows Server 2016"},
@{Version="10.0"; Build="17763.6054"; Description="Windows Server 2019"},
@{Version="10.0"; Build="20348.2582"; Description="Windows Server 2022"}
)
# 比较版本号的函数
function Compare-Versions {
param (
[string]$version1,
[string]$version2
)
$v1Parts = $version1.Split('.')
$v2Parts = $version2.Split('.')
for ($i = 0; $i -lt $v1Parts.Length; $i++) {
if ([int]$v1Parts[$i] -lt [int]$v2Parts[$i]) {
return -1
}
elseif ([int]$v1Parts[$i] -gt [int]$v2Parts[$i]) {
return 1
}
}
return 0
}
# 检查服务状态、启动类型和是否已安装
function Check-ServiceStatus {
param (
[string]$serviceName
)
$service = Get-Service -Name $serviceName -ErrorAction SilentlyContinue
if ($service -eq $null) {
return @{ IsInstalled = $false; IsRunning = $false; StartupType = "NotInstalled" }
} else {
$startupType = (Get-WmiObject -Query "SELECT StartMode FROM Win32_Service WHERE Name='$serviceName'").StartMode
return @{ IsInstalled = $true; IsRunning = $service.Status -eq 'Running'; StartupType = $startupType }
}
}
# 检查系统版本是否安全
function Check-SystemSecurity {
param (
[string]$currentVersion,
[string]$currentFullVersion,
[array]$safeVersions
)
foreach ($safeVersion in $safeVersions) {
if ($currentVersion -eq $safeVersion.Version) {
$result = Compare-Versions $currentFullVersion $safeVersion.Build
if ($result -eq -1) {
return @{
IsAffected=$true;
SafeBuild=$safeVersion.Build;
Description=$safeVersion.Description
}
} else {
return @{
IsAffected=$false;
SafeBuild=$safeVersion.Build;
Description=$safeVersion.Description
}
}
}
}
return @{
IsAffected=$null;
SafeBuild=$null;
Description="不在受检查的版本范围内"
}
}
# 输出检查结果
function Output-Result {
param (
[hashtable]$checkResult,
[hashtable]$serviceStatus
)
if ($checkResult.IsAffected -eq $true) {
if ($serviceStatus.IsRunning) {
Write-Host "当前系统版本 ($currentFullVersion) 低于安全版本 ($majorMinorVersion.$($checkResult.SafeBuild)),且 'TermServLicensing' 服务正在运行。" -ForegroundColor Red
Write-Host "系统可能受影响,需要安装补丁。" -ForegroundColor Red
} elseif ($serviceStatus.IsInstalled -eq $true -and $serviceStatus.StartupType -eq "Auto") {
Write-Host "当前系统版本 ($currentFullVersion) 低于安全版本 ($majorMinorVersion.$($checkResult.SafeBuild)),'TermServLicensing' 服务配置为自动启动但未运行。" -ForegroundColor Yellow
Write-Host "系统可能存在安全隐患,请检查服务配置或安装补丁。" -ForegroundColor Yellow
} else {
Write-Host "当前系统版本 ($currentFullVersion) 低于安全版本 ($majorMinorVersion.$($checkResult.SafeBuild)),但 'TermServLicensing' 服务未运行且未配置为自动启动。不需要安装补丁。"
}
} elseif ($checkResult.IsAffected -eq $false) {
Write-Host "当前系统版本 ($currentFullVersion) 高于或等于安全版本 ($majorMinorVersion.$($checkResult.SafeBuild))。系统是安全的。"
} else {
Write-Host "当前系统版本 ($currentFullVersion) $($checkResult.Description)。"
}
}
# 主程序逻辑
function Main {
# 获取主版本号和次版本号
$majorMinorVersion = "$($currentVersion.Split('.')[0]).$($currentVersion.Split('.')[1])"
# 检查系统版本
$checkResult = Check-SystemSecurity -currentVersion $majorMinorVersion -currentFullVersion $currentFullVersion -safeVersions $safeVersions
# 检查服务状态
$serviceStatus = Check-ServiceStatus -serviceName "TermServLicensing"
# 输出结果
Output-Result -checkResult $checkResult -serviceStatus $serviceStatus
}
# 执行主程序逻辑
Main
这个漏洞修复需要安装补丁, 这是对应的补丁包, 按照版本下载对应的补丁包即可。
但是需要注意的是, win 2012 在23年10月份停止支持了, 也就是说你安装新的月度汇总是装不上的, 需要购买ESU支持, 如果不想花钱没别的办法, 卸载远程桌面会话管理器, 就是那个可以让多个账户同时登录的那个功能, 服务名叫做 TermServLicensing 。
https://www.hugbg.com/archives/3846.html




评论